Rigorous cybersecurity qualifications that stand up to regulations
Evaluate Vendor security maturity and risk with expert-led cybersecurity assessments.
OUR FOCUS
Evaluate how a Vendor safeguards systems, data, and operational continuity with comprehensive qualification services.
Evaluate how a Vendor safeguards systems, data, and operational continuity with comprehensive qualification services.
Our expertise
Deep technical expertise for clinical environments
Leverage cybersecurity expertise from industry veteran auditors.
Stay compliant with the latest cybersecurity standards and evolving regulatory landscape.
Stay ahead of potential risk and make informed Vendor decisions.
Leverage cybersecurity expertise from industry veteran auditors.
Stay compliant with the latest cybersecurity standards and evolving regulatory landscape.
Stay ahead of potential risk and make informed Vendor decisions.
Leverage cybersecurity expertise from industry veteran auditors.
Stay compliant with the latest cybersecurity standards and evolving regulatory landscape.
Stay ahead of potential risk and make informed Vendor decisions.
Leverage cybersecurity expertise from industry veteran auditors.
Stay compliant with the latest cybersecurity standards and evolving regulatory landscape.
Stay ahead of potential risk and make informed Vendor decisions.
Our audits
Comprehensive qualification support
Our platform and team of experts enable you to apply rigorous, industry-aligned frameworks to every Vendor evaluation.
Our platform and team of experts enable you to apply rigorous, industry-aligned frameworks to every Vendor evaluation.
Our platform and team of experts enable you to apply rigorous, industry-aligned frameworks to every Vendor evaluation.
Our platform and team of experts enable you to apply rigorous, industry-aligned frameworks to every Vendor evaluation.
Cybersecurity RFI templates mapped to current regulations to ensure you’re asking the right questions of every Vendor.
SME-led risk scoring and risk intelligence to flag issues early.
Custom, regulator-aligned cybersecurity audits tailored to your study, Vendor type, and needs.
Cybersecurity RFI templates mapped to current regulations to ensure you’re asking the right questions of every Vendor.
SME-led risk scoring and risk intelligence to flag issues early.
Custom, regulator-aligned cybersecurity audits tailored to your study, Vendor type, and needs.
Cybersecurity RFI templates mapped to current regulations to ensure you’re asking the right questions of every Vendor.
SME-led risk scoring and risk intelligence to flag issues early.
Custom, regulator-aligned cybersecurity audits tailored to your study, Vendor type, and needs.
Cybersecurity RFI templates mapped to current regulations to ensure you’re asking the right questions of every Vendor.
SME-led risk scoring and risk intelligence to flag issues early.
Custom, regulator-aligned cybersecurity audits tailored to your study, Vendor type, and needs.
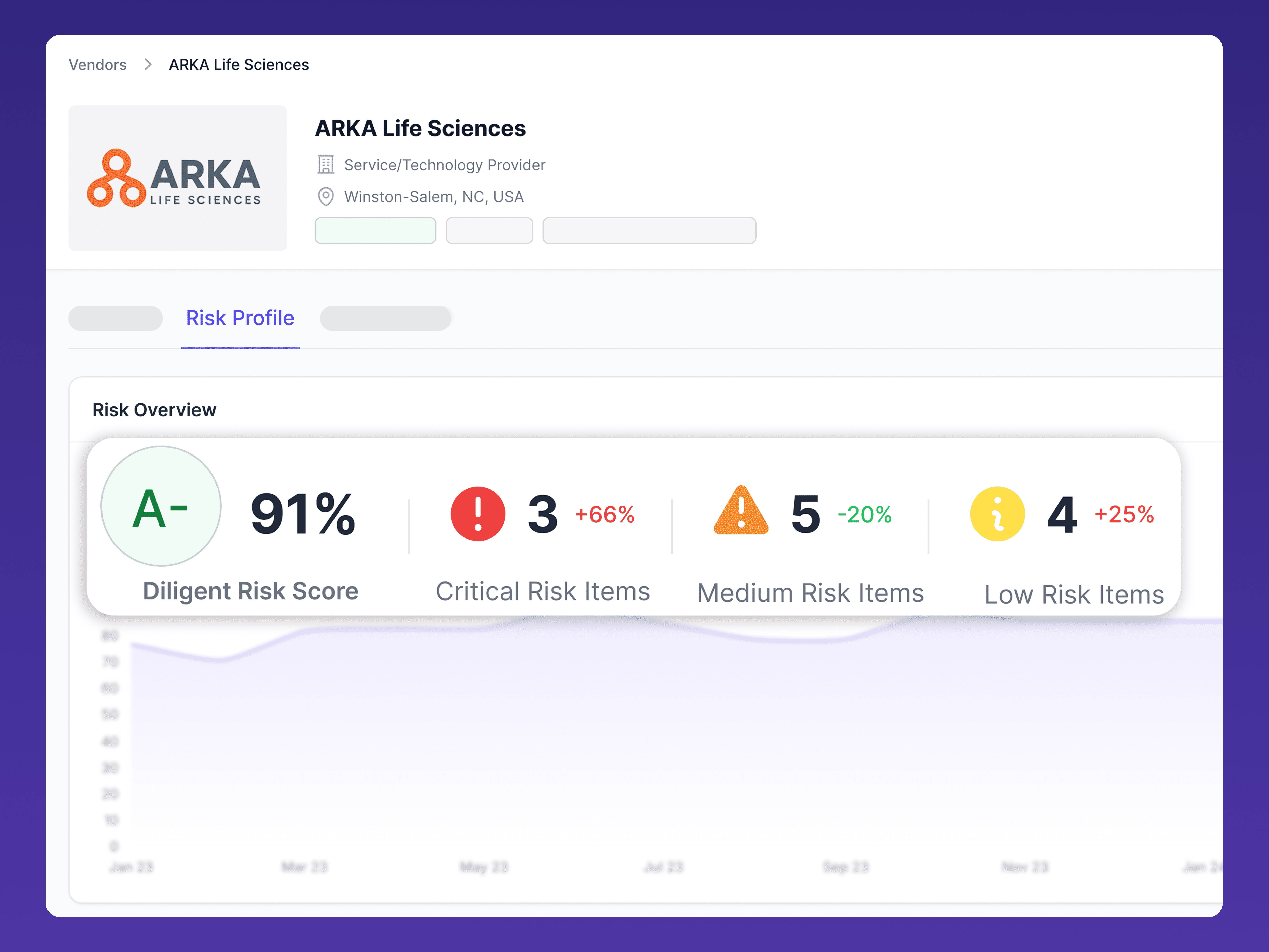


Audit Coverage
Audit coverage
Thorough, industry-aligned cybersecurity assessments
A defensible, regulator-aligned assessment of a vendor’s cybersecurity posture—mapped to clinical trial requirements, quality expectations, and global privacy regulations.
Infrastructure & Systems Security
Network architecture, segmentation, and secure configuration
Cloud infrastructure posture and shared responsibility models
Server location, hosting architecture, and geographic controls
Identity & Access Management (IAM), including MFA, RBAC & least-privilege controls
Zero-trust approach and endpoint protection
Application & Platform Security
Secure development practices (SDL/SDLC)
Vulnerability management, patching cadence, and penetration testing results
API security and third-party integrations
Change management and configuration governance
Data Privacy, Protection & Governance
Data classification, encryption at rest/in transit, and key management
Data residency and jurisdictional compliance (GDPR, HIPAA, etc.)
Customer data segregation, retention, and deletion practices
Monitoring for unauthorized access or anomalous data behavior
Operational Security & Incident Preparedness
Logging, audit trails, real-time system alarms, and firewall protections
SIEM/SOC monitoring, intrusion detection/prevention systems
Incident response plans, breach notification workflows, and root-cause analysis rigor
Business continuity planning, backup frequency, and disaster recovery capabilitiesgent offers a robust database of already-completed, up-to-date GxP qualification audit reports to enable clients to qualify new Vendors in a fraction of the time and cost. Clients can also engage our team of expert auditors for new audits tailored to specific studies or Vendors
Vendor’s Vendors (Fourth-Party Risk)
Oversight and qualification of critical hosting, processing, or software dependencies
Contracts, SLAs, and security assurances from sub-processors
Infrastructure & Systems Security
Network architecture, segmentation, and secure configuration
Cloud infrastructure posture and shared responsibility models
Server location, hosting architecture, and geographic controls
Identity & Access Management (IAM), including MFA, RBAC & least-privilege controls
Zero-trust approach and endpoint protection
Application & Platform Security
Secure development practices (SDL/SDLC)
Vulnerability management, patching cadence, and penetration testing results
API security and third-party integrations
Change management and configuration governance
Data Privacy, Protection & Governance
Data classification, encryption at rest/in transit, and key management
Data residency and jurisdictional compliance (GDPR, HIPAA, etc.)
Customer data segregation, retention, and deletion practices
Monitoring for unauthorized access or anomalous data behavior
Operational Security & Incident Preparedness
Logging, audit trails, real-time system alarms, and firewall protections
SIEM/SOC monitoring, intrusion detection/prevention systems
Incident response plans, breach notification workflows, and root-cause analysis rigor
Business continuity planning, backup frequency, and disaster recovery capabilitiesgent offers a robust database of already-completed, up-to-date GxP qualification audit reports to enable clients to qualify new Vendors in a fraction of the time and cost. Clients can also engage our team of expert auditors for new audits tailored to specific studies or Vendors
Vendor’s Vendors (Fourth-Party Risk)
Oversight and qualification of critical hosting, processing, or software dependencies
Contracts, SLAs, and security assurances from sub-processors
Infrastructure & Systems Security
Network architecture, segmentation, and secure configuration
Cloud infrastructure posture and shared responsibility models
Server location, hosting architecture, and geographic controls
Identity & Access Management (IAM), including MFA, RBAC & least-privilege controls
Zero-trust approach and endpoint protection
Application & Platform Security
Secure development practices (SDL/SDLC)
Vulnerability management, patching cadence, and penetration testing results
API security and third-party integrations
Change management and configuration governance
Data Privacy, Protection & Governance
Data classification, encryption at rest/in transit, and key management
Data residency and jurisdictional compliance (GDPR, HIPAA, etc.)
Customer data segregation, retention, and deletion practices
Monitoring for unauthorized access or anomalous data behavior
Operational Security & Incident Preparedness
Logging, audit trails, real-time system alarms, and firewall protections
SIEM/SOC monitoring, intrusion detection/prevention systems
Incident response plans, breach notification workflows, and root-cause analysis rigor
Business continuity planning, backup frequency, and disaster recovery capabilitiesgent offers a robust database of already-completed, up-to-date GxP qualification audit reports to enable clients to qualify new Vendors in a fraction of the time and cost. Clients can also engage our team of expert auditors for new audits tailored to specific studies or Vendors
Vendor’s Vendors (Fourth-Party Risk)
Oversight and qualification of critical hosting, processing, or software dependencies
Contracts, SLAs, and security assurances from sub-processors
rESOURCES
More from Diligent
Qualify innovative Vendors with speed and rigor.
Learn how you can mitigate third-party risk and stay ahead of evolving regulations.


